Maintain vIPer™ phone reliability as analog lines disappear
The simplest way to get secure phones running on IP networks
Do you have vIPer™ or STE phones using analog POTS lines? As these copper lines disappear, you need to keep your secure phones running reliably.
Perhaps you’ve tried sending vIPer™ phone modem data over VoIP, but calls keep dropping out of secure mode.
Or maybe you just aren’t sure how to make the transition and are looking for information.
VOCAL offers a reliable, tested, cost-effective solution to get your phones running on IP networks.
And our experienced engineers are available to answer your questions.
Secure phones are vital to government and military operations. They safeguard classified and sensitive information but, if the infrastructure they use is being decommissioned, the functionality they provide is at risk.
The VOCAL VoIP solution lets you keep these phones running just by subscribing and registering with our secure cloud service.
We offer a demo period, so you can test it for yourself in your environment.
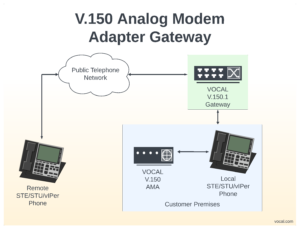
No new hardware is required for vIPer™ phones. For STE phones, simply add a VOCAL AMA for secure phones.
How do you set up secure phones to use VoIP?
vIPer™ phones:
- Configure each vIPer™ phone to use its V.150 connection following our simple configuration guide.
- Register each phone with our SPRAG.
- Use the phone as normal. Our technicians are here to help with any questions.
STE phones:
- Set up a VOCAL AMA for secure phones for each phone to encode its modem signal as V.150.1 packets.
- Register each phone with our SPRAG.
- Use the phone as normal.
Elements of the VOCAL VoIP solution
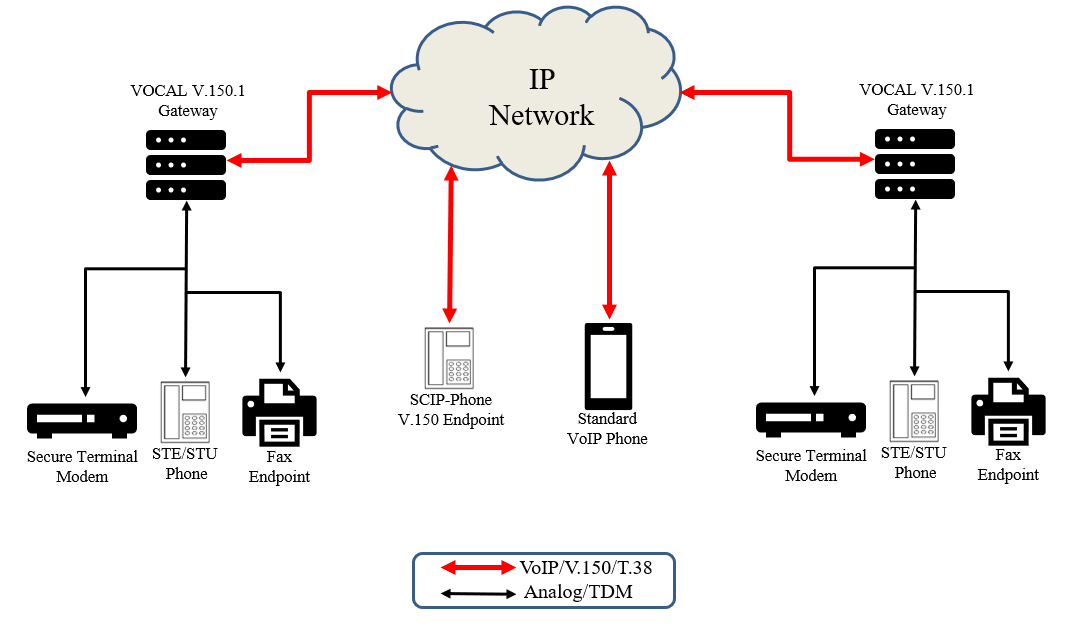
Our Secure Phone Registrar and Gateway (SPRAG) is a secure phone service for the Sectéra® vIPer™ Phone, STE, and other secure phones. It facilitates secure communications over public telephone networks.
This allows an STE phone to be used after traditional copper lines have been removed. It is a standards based approach to bridge the gap between these legacy phones and modern VoIP networks.
If you need to build your own V.150.1 Gateway, our field-tested software provides reliable, efficient transport of any type of modem signal across IP networks and adheres to the Secure Communication Interoperability Protocol (SCIP).
How does the VOCAL VoIP solution work?
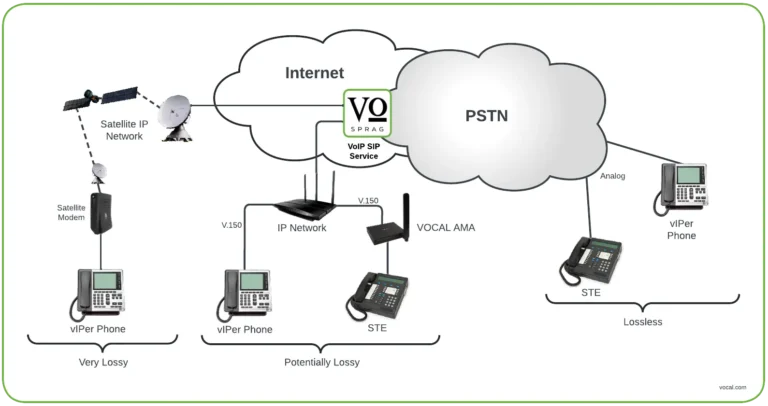
 Secure phones generally use modems to transmit encrypted audio. Where analog lines are available, the modem data is sent as a voiceband analog signal. When IP networks are the only option, the modem data must be sent in packetized form. This can be done two ways, but each way has problems.
Secure phones generally use modems to transmit encrypted audio. Where analog lines are available, the modem data is sent as a voiceband analog signal. When IP networks are the only option, the modem data must be sent in packetized form. This can be done two ways, but each way has problems.
- The modem signal is encoded as audio using a codec such as G.711. The vIPer™ soft modem uses this approach. A stream of encoded packets is sent to the far end. Most network paths experience some packet loss or delay. For voice calls, minor losses don’t have a big effect. But modems weren’t designed to cope with lost data. A secure phone call can drop back to insecure mode if data is lost, or will not be able to go secure at all.
- The modem signal is encoded using the V.150.1 Modem over IP protocol which is specifically for modems and can handle lossy networks. The V.150.1 packets are sent to the far end and then can be modulated for transport to analog connected phones. Unfortunately most telephone switches and telecom providers don’t support the V.150.1 protocol, so it can’t be used for end-to-end calls in standard phone systems.
Our SPRAG service solves these problems.
- Secure phones can use V.150.1 to talk to our server, which means lossy network connections from the phone to the server aren’t an issue.
- The SPRAG gateway converts V.150.1 to G.711 which is compatible with public telephone networks.
- G.711 packets are sent over our MPLS connection to a major domestic telecom carrier. There is no network loss in this path, so the modem signal carrying the encrypted audio is delivered intact to the far end.
Has the VOCAL solution been tested?
Yes. Our V.150.1 is SCIP-216 compliant and has been extensively tested for secure phone operations by our partners. Interoperability between vIPer™ phones and various V.150 capable switches has been tested too. The full list of switches is available on request.
We have many years of experience showing G.711 modem calls work well on major domestic carrier networks from customer deployments of our FoIP solutions.
Put our extensive knowledge of telecoms and IP modems to work for you. We’ve been in the industry for almost 40 years, and we know all about adapting to new technology.
What is a vIPer™ phone?
The Sectéra® vIPer™ Universal Secure Phone was developed by General Dynamics around 2007. These desktop phones have been providing secure calls since then, and are certified to protect classified information. They can make calls in the clear, but can also be switched to secure mode during a call. Encryption is done inside the phone. The encrypted data is sent as a modem signal. A vIPer™ phone can be used on analog and VoIP networks. They are the only VoIP phones certified to protect classified information.
STE vs vIPer™ phone – what’s the difference?
STE (secure terminal equipment) phones have been around longer than vIPer™ phones. They were developed in the 1990s by the US NSA (National Security Agency) and work on analog lines only. A separate crypto card is inserted into the phone to make secure calls. Without a crypto card, a STE phone can be used to make normal calls.
vIPer™ phones were developed by General Dynamics around 2007. They have built-in encryption and don’t need a separate crypto card. A vIPer™ phone can be connected to VoIP networks or analog lines.
How do secure phones work?
Secure phones provide end-to-end encryption using voiceband data modem technology to prevent man-in-the-middle eavesdropping. Calls are placed over the Public Switched Telephone Network (PSTN), the Defense Services Network (DSN) or other controlled access networks. Calls start with an unsecured analog voice channel that’s compatible with any general telephone. When controlled information must be discussed, the users can establish a secure connection. At this point, the two secure phones establish a modem connection that can be used for data communications. Once the data channel is established, keys are exchanged and verified, and the secure communication channel is opened.
In secure mode, voice streams are no longer analog. They are converted to a compressed digital stream using a codec such as G.729D or MELP. This allows the voice data to fit into the bandwidth of the modem connection, commonly V.32 (9600bps), and also allows the data to be secured cryptographically.
What are the problems with secure phones and VoIP?
The transition to Voice over IP is well under way and any remaining analog POTS lines are quickly being decommissioned and removed. This is a serious issue for modem-based technologies, including secure telephone equipment.
Modem protocols and implementations were carefully optimized to account for the various imperfections in analog POTS lines such as attenuation, noise and non-linearities. The longevity of these technologies shows the success of these optimizations.
VoIP has introduced a completely new set of challenges that modems weren’t designed for. Jitter, packet loss, clock phase drift, and sample slip can all result in loss of samples and periods of silence in the audio stream. Many of these impairments will cause voiceband modulation to fail which will cause the call to drop.
Technologies have been developed to adapt modems to modern VoIP networks. The most prominent of these is the V.150 Modem over IP protocol. V.150 is a demodulation-remodulation approach where the modem signal is demodulated, and the data is extracted at one of the analog-to-digital transitions. After being delivered across the IP network using SPRT, the data is remodulated at the other analog termination. This allows the data to traverse through the IP network using reliable transports and allows the modem connections to remain stable.
V.150 gateways only demodulate the data; they don’t decrypt it. This is possible because the secure phone encryption techniques operate end-to-end. Thus, there is no risk of a gateway being compromised and the voice traffic cannot be intercepted before it reaches the remote secure phone. Because of this, V.150 gateways don’t require any controlled keys or encryption technologies. V.150 is a modem relay solution for Type-1 encryption devices.
The problem with relying on V.150 is that most telephone switches and telecom providers don’t support it. So it can’t be used for end-to-end communication. This is the issue which our SPRAG service solves.
The Sectéra® vIPer™ Universal Secure Phone was developed by General Dynamics around 2007. These desktop phones have been providing secure calls since then, and are certified to protect classified information. They can make calls in the clear, but can also be switched to secure mode during a call. Encryption is done inside the phone. The encrypted data is sent as a modem signal. A vIPer™ phone can be used on analog and VoIP networks. They are the only VoIP phones certified to protect classified information.
STE (secure terminal equipment) phones have been around longer than vIPer™ phones. They were developed in the 1990s by the US NSA (National Security Agency) and work on analog lines only. A separate crypto card is inserted into the phone to make secure calls. Without a crypto card, a STE phone can be used to make normal calls.
vIPer™ phones were developed by General Dynamics around 2007. They have built-in encryption and don’t need a separate crypto card. A vIPer™ phone can be connected to VoIP networks or analog lines.
Secure phones provide end-to-end encryption using voiceband data modem technology to prevent man-in-the-middle eavesdropping. Calls are placed over the Public Switched Telephone Network (PSTN), the Defense Services Network (DSN) or other controlled access networks. Calls start with an unsecured analog voice channel that’s compatible with any general telephone. When controlled information must be discussed, the users can establish a secure connection. At this point, the two secure phones establish a modem connection that can be used for data communications. Once the data channel is established, keys are exchanged and verified, and the secure communication channel is opened.
In secure mode, voice streams are no longer analog. They are converted to a compressed digital stream using a codec such as G.729D or MELP. This allows the voice data to fit into the bandwidth of the modem connection, commonly V.32 (9600bps), and also allows the data to be secured cryptographically.
The transition to Voice over IP is well under way and any remaining analog POTS lines are quickly being decommissioned and removed. This is a serious issue for modem-based technologies, including secure telephone equipment.
Modem protocols and implementations were carefully optimized to account for the various imperfections in analog POTS lines such as attenuation, noise and non-linearities. The longevity of these technologies shows the success of these optimizations.
VoIP has introduced a completely new set of challenges that modems weren’t designed for. Jitter, packet loss, clock phase drift, and sample slip can all result in loss of samples and periods of silence in the audio stream. Many of these impairments will cause voiceband modulation to fail which will cause the call to drop.
Technologies have been developed to adapt modems to modern VoIP networks. The most prominent of these is the V.150 Modem over IP protocol. V.150 is a demodulation-remodulation approach where the modem signal is demodulated, and the data is extracted at one of the analog-to-digital transitions. After being delivered across the IP network using SPRT, the data is remodulated at the other analog termination. This allows the data to traverse through the IP network using reliable transports and allows the modem connections to remain stable.
V.150 gateways only demodulate the data; they don’t decrypt it. This is possible because the secure phone encryption techniques operate end-to-end. Thus, there is no risk of a gateway being compromised and the voice traffic cannot be intercepted before it reaches the remote secure phone. Because of this, V.150 gateways don’t require any controlled keys or encryption technologies. V.150 is a modem relay solution for Type-1 encryption devices.
The problem with relying on V.150 is that most telephone switches and telecom providers don’t support it. So it can’t be used for end-to-end communication. This is the issue which our SPRAG service solves.
Looking for more information?
Sectéra® and vIPer™ are trademarks of General Dynamics.