vIPer™ and Secure Phone Solutions
V.150.1 Solutions
The Secure Phone Registrar and Gateway (SPRAG) is a secure phone service for the Sectéra® vIPer™ Phone, STE, and other secure phones. VOCAL’s SPRAG may be used by public, private, and governmental agencies to facilitate secure phone communications over public telephone networks. Sectéra® and vIPer™ are trademarks of General Dynamics.
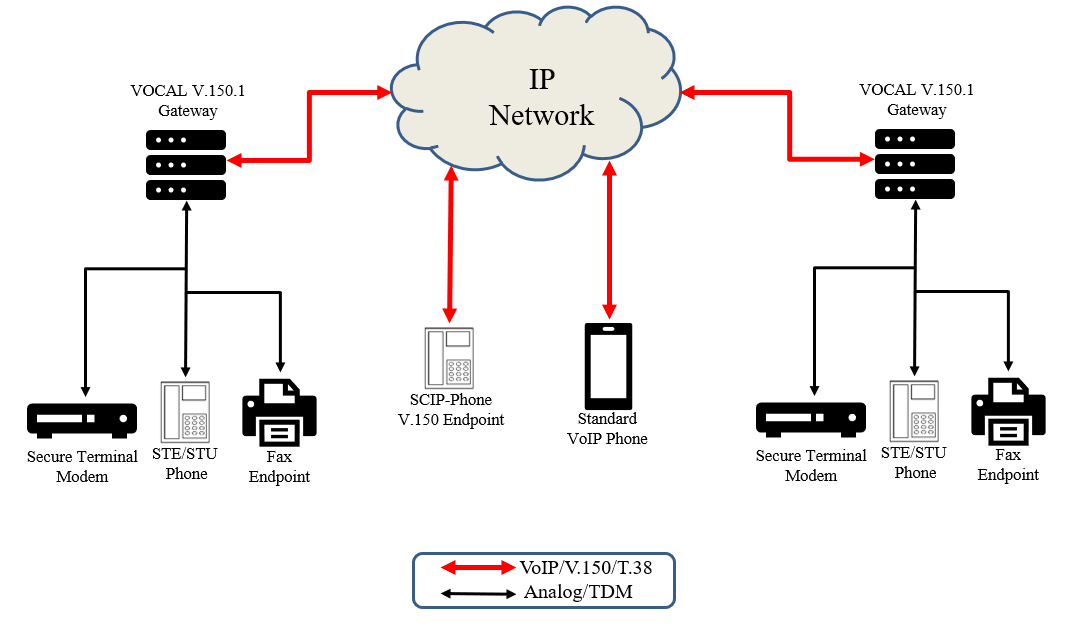
V.150.1 Gateway is a standards based implementation that incorporates reliable and efficient transport of any type of modem signal across IP networks by using Simple Packet Relay Protocol (SPRT). This solution supports modem over IP (MoIP) operation in Voice Band Data (VBD) and Modem Relay (MR) mode.
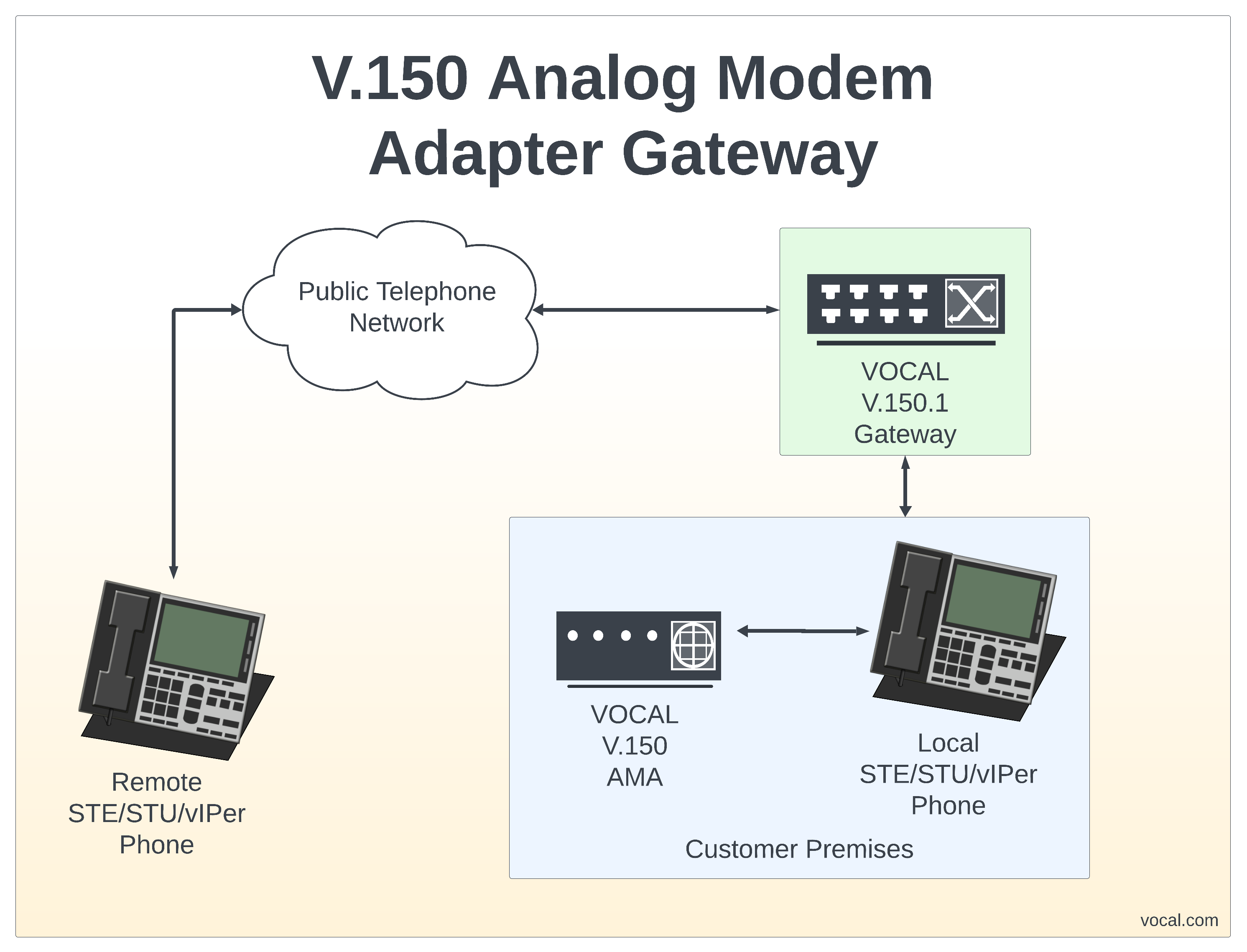
V.150 Analog Modem Adaptor for Secure Phones allows STE phone users to continue utilizing their devices after traditional copper lines have been removed. The V.150 AMA uses a standards based approach to bridge the gap between legacy STE phones and modern VoIP networks.
Secure phones are a vital part of government and military operations. They ensure the safeguarding of classified and sensitive information when it must be communicated and discussed between individuals. Secure phones such as traditional STE phones and the more modern vIPer™ phones provide end to end encryption to the call that prevents any man-in-the-middle eavesdropping from adversaries which could lead to dissemination of sensitive information.
Sectéra® and vIPer™ are trademarks of General Dynamics.
How do secure phones work?
Secure phones rely on voiceband data modem technology to achieve the encrypted connection. Calls are placed over the Public Switched Telephone Network (PSTN), the Defense Services Network (DSN) or other controlled access networks. The calls start with an unsecured analog voice channel that is compatible with any general telephone. When controlled information must be discussed, the users can establish a secure connection. At this point, the two secure phones will establish a modem connection that can be used for data communications. Once the data channel is established, keys are exchanged and verified, and the secure communication channel is opened.
While operating in secure mode, the voice streams are no longer analog. Instead, the analog streams are converted to a compressed digital stream using a codec such as G.729D or MELP. Not only does this digital conversion and compression allow the voice data to fit into the bandwidth of the modem connection, commonly V.32 (9600bps), it also allows the data to be cryptographically secured.
What are the problems with vIPer™ (Secure) phones and VoIP?
 The transition to Voice over IP is well underway and the remaining analog POTS lines are quickly being decommissioned and removed. This is posing a serious issue for modem-based technologies, including secure phones.
The transition to Voice over IP is well underway and the remaining analog POTS lines are quickly being decommissioned and removed. This is posing a serious issue for modem-based technologies, including secure phones.
Modem protocols and modem implementations were carefully designed and optimized to account for the various impurities present in analog POTS lines such as attenuation, noise, non-linearities, etc. The longevity of these technologies is a testament to the success of these optimizations. However, VoIP has introduced a completely new set of impurities that modems were simply not designed for.
Jitter, packet loss, clock phase drift, sample slip, etc. can all result in loss of samples and periods of silence in the audio stream that modem designers simply could not have foreseen. Many of these impairments will cause the modulation, and thus the call, to fail completely.
How can vIPer™ phones be used over VoIP?
Luckily, technologies have been developed to adapt modems to modern VoIP networks. The most prominent of these is the V.150 Modem over IP protocol. V.150 is a demodulation-remodulation approach where the modem signal is demodulated, and the data is extracted at one of the analog-to-digital transitions. After being delivered across the IP network using SPRT, the data is remodulated at the other analog termination. This allows the data to traverse through the IP network using reliable transports and allows the modem connections to remain stable.
V.150 gateways only demodulate the data; they do not decrypt it. This is possible because the secure phone encryption techniques operate end-to-end. Thus, there is no risk of a gateway being compromised and the voice traffic cannot be intercepted before it reaches the remote secure phone. Because of this, V.150 gateways do not require any controlled keys or encryption technologies. V.150 is a modem relay solution for Type-1 encryption devices.
VOCAL’s Solutions for Secure Phones
VOCAL offers several solutions for using secure STE and vIPer™ phones over modern VoIP networks.
The Secure Phone Registrar and Gateway (SPRAG) is a secure phone service offered by VOCAL Technologies for the Sectéra® vIPer™ Phone and other secure phones. VOCAL’s SPRAG may be used by public, private, and governmental agencies to facilitate secure phone communications over public telephone networks. VOCAL’s SPRAG service augments the public telephone network by serving as a gateway between the V.150.1 protocol used by these secure phones and V.32/V.34 modem communications over G.711 on the public telephone network.
VOCAL’s V.150.1 gateway enables the conversion between V.150.1 and traditional voiceband data connections. The V.150.1 gateway is designed to run on standard Windows, Linux, and Cloud platforms and connect to a Voice over IP provider to deliver the voiceband data leg of the call. VOCAL’s modem technology is utilized in the V.150.1 gateway including optimizations for transporting modem connections over VoIP networks. The gateway conforms to the SCIP-216 portions of the V.150.1 protocol making it ideal for secure phone applications. It is compatible with other V.150 gateways and it is also compatible with V.150 endpoints such as vIPer™ phones. VOCAL’s V.150.1 gateway solution adheres to ITU-T V-Series recommendations to be DoD compliant,
VOCAL’s Analog Modem Adapter (AMA) also operates as a V.150.1 gateway but rather than connecting to a VoIP network, it features an RJ-11 FXS port that can connect directly to the STE and vIPer™ phones. The AMA provides dial tone, line voltage, and ringing signal for the secure phone and eliminates the need for physical analog lines. The AMA operates like a modem aware ATA device. The AMA can be used with analog (RJ-11) connected vIPer™ phone or it can be used with a legacy STE/STU secure phone. The AMA implements the SCIP-216 portions of the V.150 protocol so it is compatible with other V.150 implementations including VOCAL’s V.150.1 gateway. VOCAL’s V.150.1 Gateway and Analog Modem Adapter solutions are Cloud hosting compatible.

VOCAL’s solution is available for the above platforms. Please contact us for specific supported platforms.

Please contact us for more information about solutions for Secure Phones.