- Establish CHILD-SAs for Encapsulated Security Payload (ESP) Protocol and/or Authentication Header (AH) Protocol
- Defines the cryptographic algorithms to be used by the SAs
IKEv2 is a request/response pair protocol. These pairs are refered to as exchanges. The requester bears the burden of ensuring reliability. If a response is not received the requester can either retransmit or abandon the connection. IKEv2 has four types of exchanges:
- IKE_SA_INIT– This is the first exchange that establishes the IKE-SA and MUST complete before any further exchanges can happen. It performs three functions in the setup of the IKE-SA.
- Negotites security parameters for the IKE-SA
- Sends nonces
- Sends Diffie-Hellman values
- IKE_AUTH– This is the second exchange and MUST complete before any further exchanges can happen. It performs three required functions:
- Transmits identities
- Proves knowledge of the secrets related to those identities
- Establishes the first, and usually the only, AH and/or ESP CHILD-SA
- CREATE_CHILD_SA – This is simply used to create additional CHILD-SAs as needed
- INFORMATIONAL– This is a maintenance exchange that performs a veriety of functions to maintain the SAs. Some of these function include:
- Delete SAs as needed
- Report error conditions
- Check SA liveliness
- Other SA housekeeping functions
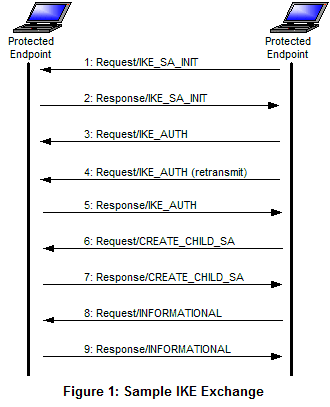
Once the first two mandatory exchanges have completed in their proper order, all subsequent exchanges can happen in any order necessary. In some cases their will be no future exchanges once everything is setup. An example IKEv2 exchange is shown in Figure1.
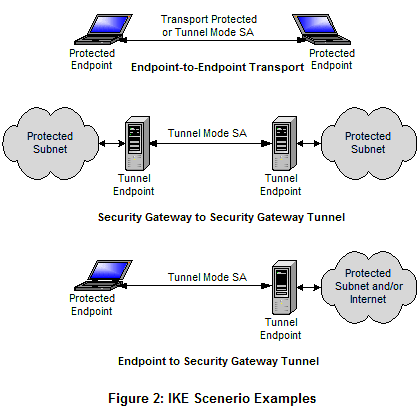
IKEv2 is expected to operate in a veriety of scenarios, examples of threescenarios can be seen in Figure 2. The Endpoint to Endpoint Transport scenario (upper diagram) shows both the endpoints implementing IPsec. This senario can use either transport or tunnel mode. The middle diagram shows Security Gateway to Security Gateway Tunnel scenario. This is a case where the endpoints do not implement IPsec but nodes between the endpoints do. This implementation is completely transparnt to the users. The last diagram shows an example of Endpoint to Security Gateway Tunnel scenario where a endpoint implementing IPsec connects to a Security Gateway to securly access the network on the other side. Others senarios are possible and can include a combination of the three shown.
IKEv2 employs a number of cryptographic protocols to accomplish all the security requirements of Key Management. IKEv2 is based on the Diffie-Hellman (DH) Key Management Protocol. IKE has four transform types that are mandatory to implement:
- Ecryption Algorithms – Common algorithms
DES,
3DES, RC5, IDEA, 3IDEA,
CAST, BLOWFISH, and
AES - Pseudo-Random Functions – Common functions
HMAC and
AES - Integrity Algorithms – Common Algorithms
HMAC,
DES, KPDK, and
AES - Diffie-Hellman Groups – Defined Groups are 2, 3, 5, and 14 through 18