VOCAL’s Secure SIP implementation is based on requirements and recommendations specified in RFC3261 and RFC3329. VOCAL’s TLS implementation by default is built upon OpenSSL, but can be configured for other SSL implementations such as wolfSSL.
Session Initiation Protocol is an application-layer control protocol that can establish, modify, and terminate multimedia sessions and the integrity of call signaling is of the utmost importance. Clear text SIP is vulnerable to eavesdropping, man-in-the-middle (MITM) attacks, and gaining unauthorized access to VoIP networks. As the most basic level of security, VOCAL’s SIP stack supports Message Digest (MD5) authentication. This provides a basic authentication challenge between a SIP proxy server and SIP user agent. Secure Multipurpose Internet Mail Extensions (S/MIME) can be implemented to encrypt data directly within SIP messages, but its support has not been widely deployed because of the required public-key infrastructure support and the added complexity of managing security certificates. However, running SIP over TLS does provide a comprehensive level of security over a single hop. Since it is very common for a SIP call to traverse multiple proxy servers from one end to the other, there is a need to guarantee end-to-end security for SIP traffic. In order to assure this end-to-end security, SIP provides a secure URI scheme called SIPS (Secure SIP).
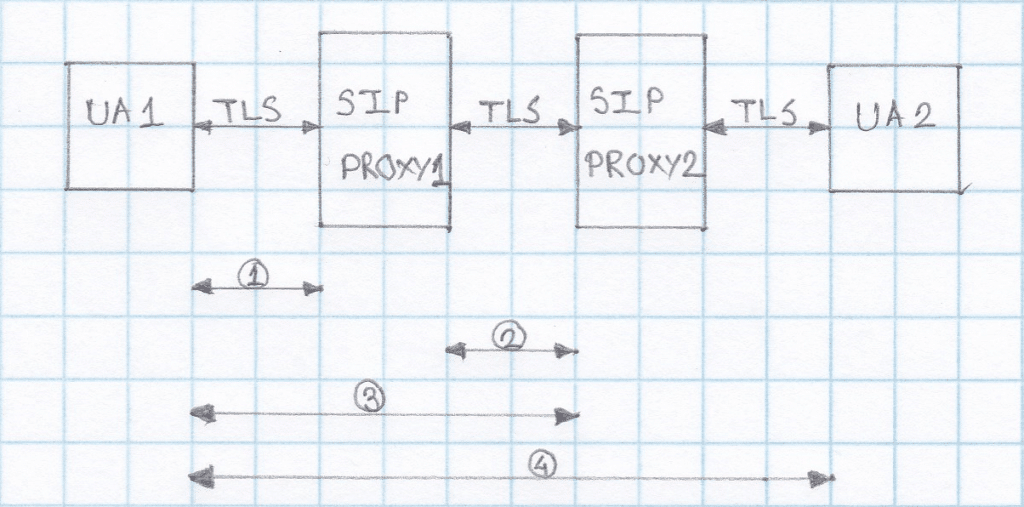
If a SIP User Agent, UA1, wants to establish a secure SIP session with UA2:
- UA1 contacts proxy server1 requesting a TLS session along with a session invitation for UA2. The proxy server provides a public certificate and UA1 validates it. UA1 and proxy server1 exchange session keys to encrypt/decrypt data for that particular session.
- Proxy server1 forwards the session invitation to the next proxy server using a TLS session or IPSec mechanism.
- UA1 and proxy server2 authenticate over TLS. The same procedure is repeated till the last hop ensuring SIP over TLS is used end-to-end.
- The secured session between UA1 and UA2 is now established.
Questions might arise about the use of a security protocol to make secure end-to-end connection between UAs (possibly IPSec). Because of the fact that SIP proxy servers need to interpret and modify certain header fields in SIP messages, end-to-end encryption is not a feasible option. Since TLS is a lighter weight protocol and more easily managed than IPSec, we use TLS for SIP-based communications. A call to a SIPS URI is guaranteed to be encrypted from end to end. All SIP traffic within this call will be secured using TLS from the sender to the domain of the final recipient. Once a SIP message reaches the domain of the final recipient, it will be securely sent to the final destination. However, it is not mandatory that TLS be used. The security mechanism for this last hop is determined by the domain of the final destination.
More Information
- Session Initiation Protocol (SIP)
- VoIP Software
- VoIP Design
- WebRTC and SIP
- WebRTC Communication Security
- RFC 3261 Standard
- SIP Analog Modem Server (SAMS)
- The Transport Layer Security (TLS) Protocol Version 1.3
- SIP Software Modules
- SIP Conferencing
- SIP Message Routing
- SIP Presence and Instant Messaging
- SIP Registration
- SIP User Authentication
- Secure SIP
- Session Initiation Protocol (SIP) and Deep Packet Inspection (DPI)
- SIP Trunking
VOCAL Technologies has been in business for over 30 years and is an engineering design house that can provide a custom solution that meets your unique communication requirements.
Please contact us to discuss your communication application requirements.