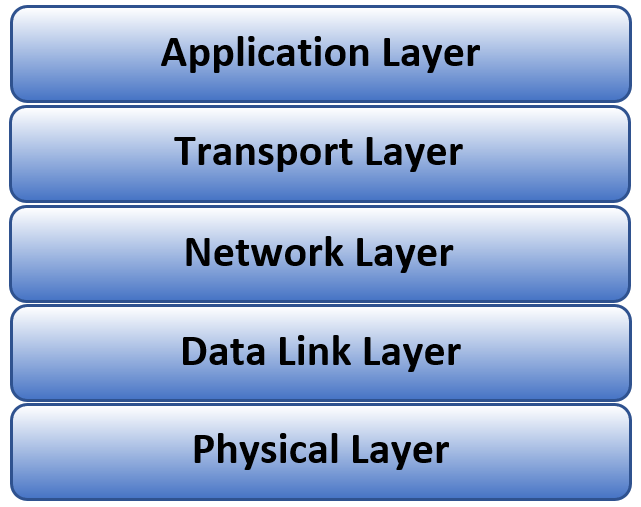
Each layer of the TCP/IP stack (Application, Transport, Network, Data Link and Physical) has established security and cryptography schemes except one, the Physical (PHY) layer.
- The Application Layer
- Users directly interface with this level. Applications include email clients, internet browsers, video conferencing.
- Security is provided by encrypting the data to be sent. Secure Real-time Transport Protocol (SRTP) is example protocol initiated at this layer.
- The Transport Layer
- Manages communications sessions between host and destination devices.
- Transport Layer Security protocol doesn’t exactly fit into the Transport layer as it is used by the user application, but it establishes a secure communication between the sender and receiver through a handshaking procedure.
- Network Layer
- Is responsible for routing IP data packets across the network.
- The IPsec protocol provides data origin authentication, replay protection at this layer.
- Data Link Layer
- Controls access to the communication network.
- Protocols such as Wi-Fi Protected Access (WPA) provides security by only allowing access to the network for the MAC addresses that have been verified.
- Physical Layer
- Is the physical (wireless, fiber optical, electrical) transmission of the data from the upper layers
- No established security standard or protocol
Physical Layer Security (PLS) has been an area of active research for wireless communication systems. Many of the potential solutions are multi-antenna-based utilizing spatial diversity of the physical medium. Transmit beamforming utilizes multiple antennas to direct a beam in a desired direction, reducing the SNR of an eavesdropper. This solution is especially attractive on mmWave networks because of the ability to create narrow beams from small antenna arrays.