There are two classes of JPSEC tools normative and non-normative. The normative are defined with the protection method templates specified in the tool syntax. Non-normative tools are also called JPSEC Registration Authority (RA) tools or JPSEC User-Defined Tools and are registered with the RA or are provided by the user. The non-normative can use the normative templates or can define there own as appropriate. The tools are used to implement security functions. JPSEC is designed as an open framework in order to make it easily extensible. Current tools concentrate on these security services:
- Confidentiality using encryption and selective encryption
- Integrity Verification
- Image Data Integrity (Fragile Image Verification) – even one error causes verification failure
- Image Content Integrity (Semi-Fragile Image Verification) – even some incidental alteration of the image data still results in a successful verification as long as visually (perceptually) the image is unchanged
- Source Authentication
- Conditional Access
- Registered Content Identifier
- Secure Scalable Streaming and Secure Transcoding
JPSEC tools are specified in the syntax of the SEC marker. The basic tool syntax is shown in Figure 1. The syntax is interpreted differently depending on whether the tool is normative or non-normative. Table 1 shows how the syntax is interpreted for each class of tool (nt = number of tools).
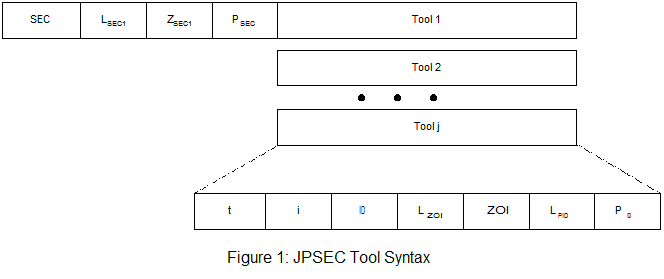
Table 1: JPSEC Tool Parameter Values
| Parameter | Normative Size (bits) | Non-Normative Size (bits) | Normative Values | Non-Normative Values | Description |
|---|---|---|---|---|---|
| t | 8 | x0xx xxxxb | x1xx xxxxb | Tool instance index (can be used as a unique identifier) | |
| i | 8 + 8 * nt | 0…(27+7*nt – 2) (27+7*nt – 1) is reserved | Length of Marker Segment in Bytes | ||
| ID | 8 | Variable | see Table 2 | see Figure 3 | Identification value for the JPSEC tool |
| LZOI | 16 + 8 * nt | 0…215+7*nt | Length of ZOI in bytes | ||
| ZOI | Variable | Variable | Zone of Influence for the JPSEC tool | ||
| LPID | 16 + 8 * nt | 0…215+7*nt | Length of PID in bytes | ||
| PID | Variable | see Figure 2 and Table 3 | Managed by RA or User | Parameters for JPSEC tool | |
JPSEC normative tools are based on protection method templates defined in the standard. The tool identifier ID is used to identify which template is used (see Table 2). Figure 2 shows the parameters (PID) syntax for normative tools with the description of each field in Table 3.
Table 2: Normative Tool Template ID Values
| Value | Protection Method Template |
|---|---|
| 0 | Reserved |
| 1 | Decryption Template |
| 2 | Authentication Template |
| 3 | Hash Template |
| 4 | NULL Tool |
| All other values are reserved for ISO use |

JPSEC normative tools are based on protection method templates defined in the standard. The tool identifier ID is used to identify which template is used (see Table 2). Figure 2 shows the parameters (PID) syntax for normative tools with the description of each field in Table 3.
Table 3: Normative Tool Parameter Values
| Parameter | Size (bits) | Values | Description |
|---|---|---|---|
| TID | Variable, if t=0 and ID=1 | see Decryption Template | Template parameters for normative tool with template identifier ID |
| Variable, if t=0 and ID=2 | see Authentication Template | ||
| 16, if t=0 and ID=3 | see Hash Template | ||
| 0, if t=0 and ID=4 | NA | ||
| Unknown, if t=0 and ID=0 or ID>4 | Reserved | ||
| PD | Variable | see below | Processing Domain for normative tool |
| G | 24 | see below | Granularity for normative tool |
| V | Variable | see below | Value list for normative tool dependent on template identifier ID |
The Processing Domain (PD) is used to describe the domain the JPSEC tool is applied. There are four possible domains
and depending on the domain a few specifics related to the field parameters. The four domains are:
- Pixel Domain
- Wavelet Coefficient Domain
- Quantized Wavelet Coefficient Domain
- Codestream Domain
If the Wavelet Coefficient Domain or the Quantized Wavelet Coefficient Domain are where the JPSEC tool is being applied it can either be applied on the sign bit or the most significant bit. When the Codestream Domain is where the tool is being applied it can either be applied on both the packet header and body or just on the packet body.
The Granularity (G) indicates the unit of protection for each method by specifying the order the elements are processed along with granularity level. There are a total of twelve granularity levels.
- Tile
- Tile-part
- Component
- Resolution Level
- Layer
- Precinct
- Packet
- Sub-band
- Code-block
- Total area identified by Zone of Influence (ZOI)
- Item identified in non-image-related ZOI
- Zone identified in non-image-related ZOI
The Value List (VL) field specifies values that change as the tool is applied and the granularity of the change. Values specified include keys, Initialization Vectors (IV), MAC values, Digital Signatures (DS), and hash values. The Zone of Influence (ZOI) is used describes the coverage are of the JPSEC tool, referred to as the influenced data.
JPSEC non-normative tools have the flexibility of either using some of the pre-defined structures in the JPSEC normative tools or defining there own as needed. There are two classes of non-normative tools
- JPSEC Registration Authority (RA) Tools – the signaling for these tools is specified using the RA
- JPSEC User-Defined Tools – the signaling for these tools is specified by the application/user
These classes of tools use a 32-bit ID value to show if it is a RA tool (0x0000 0000 to 0x7FFF FFFF), user defined
tool (0x8000 0000 to 0xEFFF FFFF) or reserved (0xF000 0000 to 0xFFFF FFFF). The ID value also has a name space
parameter that specifies the name space of the specification. The PID field is not fully defined in these
instances in the standard. If the tool is an RA tool then the RA defines the PID and if a user tool then
it is defined by the user.
Further information available here:
- JPSEC
- JPSEC Tool Decryption Template
- JPSEC Tool Authentication Template
- JPSEC Tool Hash Template
- JPSEC Tool Key Template
JPSEC Standards available here:
- Joint Photographic Experts Group (JPEG) Part 8 – JPSEC: Secure JPEG 2000 Final Committee Draft
- ISO/IEC 15444-8:2007 – Information technology — JPEG 2000 image coding system: Secure JPEG 2000
- T.807 (05/06) – Information technology — JPEG 2000 image coding system: Secure JPEG 2000