Digital images are used widely by individuals, corporations, and government agencies to convey important, and sometimes secure, information. The advances in Internet, web, email and computer technologies have made them easy to make and distribute compared to classic paper-based images. The newest standard published by the Joint Photographic Experts Group (JPEG) committee is JPEG2000 and has many advantages over the currently used JPEG standard. The major problem with digital images is that they are easy to copy, alter and distribute for both legal and illegal purposes. With this in mind there has been a high demand for a security solution for JPEG2000. In response the JPEG committee has created a security part (Part 8: Secure JPEG 2000) of the JPEG2000 standard also referred to as JPSEC.
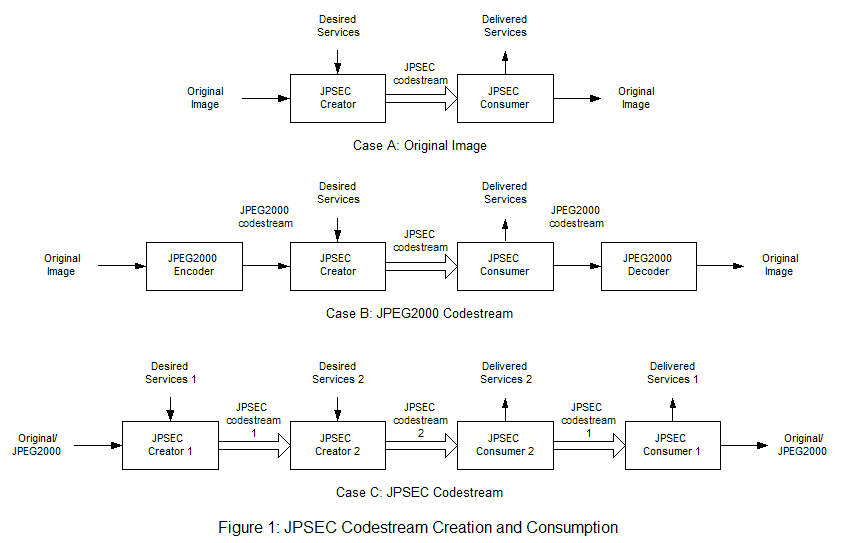
The JPSEC standard defines the framework, concepts and methodology for securing JPEG 2000 images. At the center of the JPSEC standard is the specification of a syntax targeted toward JPEG 2000 coded data and allows protection of either the entire code stream or just segments. The syntax specifies what security services are associated with the image data, which JPSEC tools are required for each service, how to apply the tools, and which parts of the image data are protected. The protected data is referred to as the JPSEC codestream. The JPSEC codestream can be created from the original image (Figure 1: Case A), a JPEG 2000 codestream (Figure 1: Case B) or another JPSEC codestream (Figure 1: Case C). Case C is important in the fact that it allows multiple JPSEC tools to be applied to the codestream.
There are two classes of JPSEC tools normative and non-normative. The normative are defined with the protection method templates supplied in the JPSEC standard. Non-normative tools are also called JPSEC Registration Authority (RA) tools or JPSEC User-Defined Tools and are registered with the RA or are provided by the user. The non-normative can use the normative templates or can define there own as appropriate. The tools are used to implement security functions. JPSEC is designed as an open framework in order to make it easily extensible. Current tools concentrate on these security services:
- Confidentiality using encryption and selective encryption
- Integrity Verification
- Image Data Integrity (Fragile Image Verification) – even one error causes verification failure
- Image Content Integrity (Semi-Fragile Image Verification) – even some incidental alteration of the image data still results in a successful verification as long as visually (perceptually) the image is unchanged
- Source Authentication
- Conditional Access
- Registered Content Identifier
- Secure Scalable Streaming and Secure Transcoding
JPSEC signaling is done through the flexible syntax of SEC markers. They are located in the main header and allows for the description of all required information for securing JPEG 2000 images. It provides the references for each tool used, normative and non-normative, along with handling any parameters related to the tools. Figure 2 shows the syntax of the SEC marker and associated parts. A single SEC marker can be used or multiple SEC markers depending on the need. Notice that the PSEC parameter is only in the first SEC marker and defines the parameters for the entire codestream. (ns = number of marker segments, nt = total number of tools)
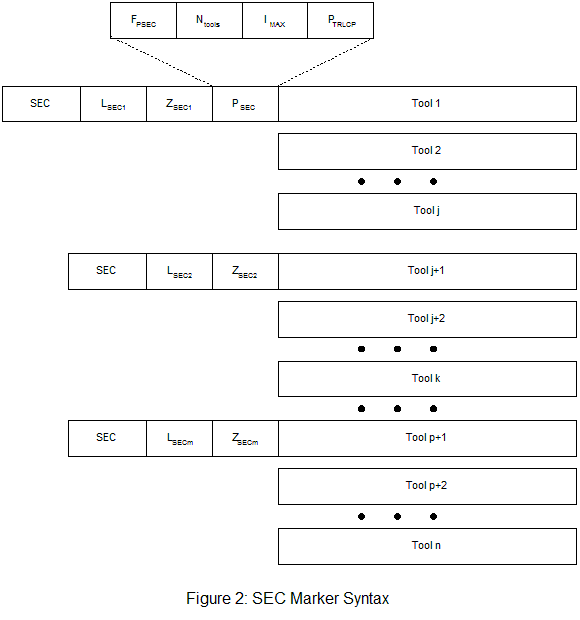
Table 1: Definitions of Main SEC Marker
| Parameter | Size (bits) | Values | Description |
|---|---|---|---|
| SEC | 16 | 0xFF65 | Marker code |
| LSEC | 16 | 2…(216 – 1) | Length of Marker Segment in Bytes |
| ZSEC | 8 + 8 * ns | 0…27+7*ns | Index of this marker segment relative to all other marker segments in header |
| PSEC | 0, if ZSEC>0 Variable otherwise | If ZSEC=0 see Table 2 | Parameter field for codestream security parameters |
| Tool i | Variable | see JPSEC tools | Parameter for JPSEC tool i |
Table 2: Definitions of Codestream Security Parameters (PSEC)
| Parameter | Size (bits) | Values | Description |
|---|---|---|---|
| FPSEC | Variable | see description | Flag to indicate if INSEC marker is used (bit 1), if multiple SEC markers are used (bit 2), if original JPEG 2000 part 1 codestream was modified (bit 3) and if TRLCP is defined (bit 4) |
| Ntools | 8 + nt * 8 | 1…27+7*nt | Number of JPSEC tools used in the codestream |
| IMAX | 8 + nt * 8 | 0…27+7*nt | Maximum tool index value used in the codestream |
| PTRLCP | 0, if FTRLCP=0 32, if FTRLCP=1 | see Table | Parameter field to define the format of the TRLCP tag |
A structure called a TRLCP tag is defined to uniquely identify a JPEG 2000 packet. The tag syntax is shown in Figure 3 and the parameters are defined in Table 3. A packet can be uniquely identified by:
- tile index
- Resolution level index
- Layer index
- Component index
- Precinct index
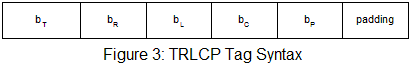
Table 3: Definition of TRLCP Tag Syntax
| Parameter | Size (bits) | Values | Description |
|---|---|---|---|
| bT | 8 | 0…(28 – 1) | Number of bits to represent tile index is bT + 1 |
| bR | 4 | 0…15 | Number of bits to represent resolution level index is bR + 1 |
| bL | 5 | 0…31 | Number of bits to represent layer index is bL + 1 |
| bC | 5 | 0…31 | Number of bits to represent component index is bC + 1 |
| bP | 8 | 0…(28 – 1) | Number of bits to represent precinct index is bP + 1 |
Further information available here:
JPSEC Tool Decryption Template
JPSEC Tool Authentication Template
JPSEC Registration Authority (RA)
JPSEC Standards available here:
Joint Photographic Experts Group (JPEG) Part 8 – JPSEC: Secure JPEG 2000 Final Committee Draft
ISO/IEC 15444-8:2007 – Information technology — JPEG 2000 image coding system: Secure JPEG 2000
T.807 (05/06) – Information technology — JPEG 2000 image coding system: Secure JPEG 2000