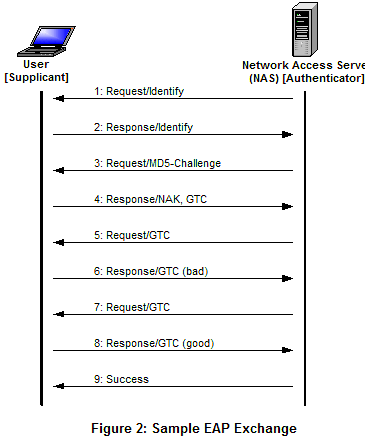
Extensible Authentication Protocol (EAP) is an authentication protocol used in PPP and 802.11 connections that can support multiple authentication mechanisms. IEEE 802.1x is based on EAP and is referred to as EAPoL (EAP over LAN). EAPol is used by EAPoW (EAP over Wireless) in the 802.11 standard to distribute WEP keys. EAP is a simple encapsulation that can run over any link layer.
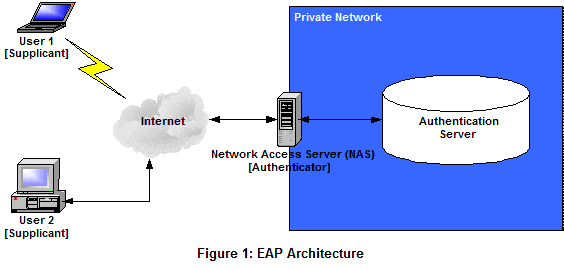
EAP Architecture
There are three main components to the authentication conversation:
- Supplicant (client software)
- Authenticator (access point)
- Authentication Server (a RADIUS/AAA server)
EAP Packet Format
| Code | Identifier | Length | Data |
|---|---|---|---|
| 1 byte | 1 byte | 2 bytes | variable length |
The EAP packet can be carried in any type of frame (e.g. on PPP links it is carried in a PPP frame with a protocol number 0xC227). The fields in the packets are:
Code
The Code field is one byte long and is used to interpret the Data field by identifying the type of EAP packet.
| Code | Description | Reference |
|---|---|---|
| 0 | – | – |
| 1 | Request | RFC 3748 |
| 2 | Response | RFC 3748 |
| 3 | Success | RFC 3748 |
| 4 | Failure | RFC 3748 |
| 5 | Initiate | RFC 5296 |
| 6 | Finish | RFC 5296 |
| 7-255 | – | – |
Identifier
The Identifier field is one byte long and contains an unsigned integer used to match requests with responses. Each new transmission uses a new Identifier number.
Length
The Length field is two bytes long and contains the number of bytes in the entire packet. EAP assumes anything in excess of the Length is padding that can be ignored.
Data
The Data field has a variable length (including zero bytes). The value of the Code field defines the way the Data field is to be interpreted.
EAP Request and Response Packet Format
| Code | Identifier | Length | Type | Type-Data |
|---|---|---|---|---|
| 1 byte | 1 byte | 2 bytes | 1 byte | variable length |
The Authenticator sends requests to the system seeking access and the responses grant or deny access. These equests, Code field equal to 1, and responses, Code field equal to 2, compose EAP exchanges. The Identifier and Length fields are used as described previously.
Type
The Type field is one byte long and defines the type of request or response. Only one type is used in each packet and the response Type matches the request Type except if the request is unacceptable, in this case the peer can send a NAK to suggest an alternative Type.
Table of valid Type values and reference information
Type Data
The Type-Data field has a variable length and the value of the Type field defines the way the Authenticator interprets Type-Data.
EAP Success and Failure Packet Format
| Code | Identifier | Length |
|---|---|---|
| 1 byte | 1 byte | 2 bytes |
Once the Authenticator determines the exchange is complete it issues a success or failure frame to end the EAP exchange. The Code will either be 3 for success or 4 for failure and the Length will always be 4 for this packet.