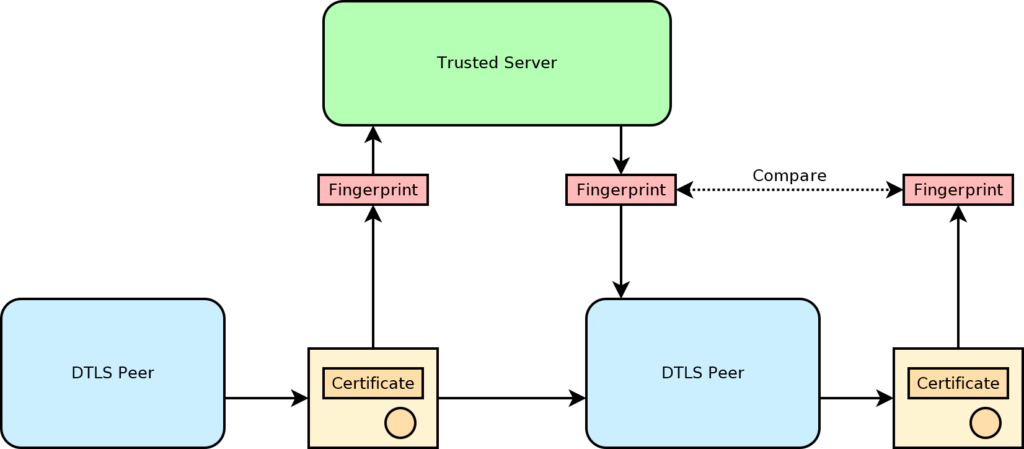
A DTLS fingerprint is a way for the two endpoints of a DTLS connection to verify each other’s identity even if self-signed certificates are used in the TLS handshake. The proper way to verify the far end’s identity is to use a public key infrastructure with certificates that are signed by trusted certificate authorities. This is generally very difficult for DTLS connections which may be established between two peers that do not have their own domain names to verify. In this case, the connection is mediated by a server that does have a proper domain name and can be properly verified. This establishes a trusted communication link between the two peers, usually through a standard TCP/TLS link. Messages sent through this link are relayed to the peers through the server.
To establish a DTLS connection, the two endpoints first generate their own certificates. Next, they run the certificates through a hashing algorithm to generate the fingerprints. The certificates are sent through the DTLS connection directly to the other endpoint. The fingerprints are sent through the trusted link. Once this exchange is done, each endpoint can verify the authenticity of the peer’s certificate by running the same hash and comparing the result to the fingerprint received through the trusted link. If the hash matches the fingerprint, then the certificate must have been generated by the DTLS peer, and the peer’s identity is confirmed.