Watermarking is a technique for the insertion of side information, defined by the information’s owner, into the source (cover) information. It is widely utilized in image/video applications.
Digital watermarking has a goal of hiding the owner’s visual information in the source visual information. The purpose of digital watermarking is different from other techniques, such as steganography, where the goal is to hide information in the source visual information in such a way that the information is not possible to detect.
Digital watermarking, on the other hand, is embedded so that the information becomes virtually indistinguishable for users of the source information. Although detectable, it is not possible to remove the hidden information even by applying strong transformation of the watermarked information.
Watermarking Types
There are different types of watermarking including visible, invisible and dual. A visible watermark is clearly visible on a watermarked image/video, whereas an invisible watermark is hidden and virtually indistinguishable from the image/video. Dual watermarking is a combination of visible and invisible.
Watermarks can also be classified as one of two types, noise or image/video. A Noise type is based on pseudo noise information such as Gaussian or chaotic sequences. An Image/Video type has watermark information represented as an image or motion image, usually a binary image that represents a stamp, logo or label.
Watermarking Domains
Algorithms for watermarking may be based on a spatial domain or a transformed domain. Spatial domain watermarking modifies the pixel values of one or many randomly selected subsets of images. It directly loads the raw data into the image pixels. It could be based on using different patches or least significant bit planes. Transform domain watermarking is based on transform coefficient alteration. There are several commonly used transform domain methods, such as DCT or DWT.
Watermarking Procedures
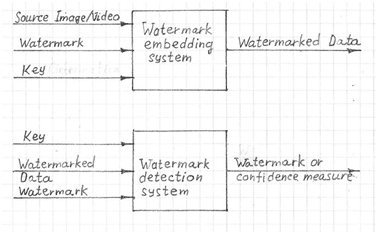
Watermarking procedures are based on using key information. They require a user key during both the insertion and the extraction procedures. If the correct key is specified in the watermark extraction procedure it returns the right watermark. If the key is incorrect the extracted watermark looks like random noise. The conventional digital watermark systems use a technique like common-key cryptography. There are both secret and public key authentication watermarking schemes.
According to the key usage, the watermarking could be symmetric or asymmetric. In symmetric watermarking the same keys are used for embedding and detecting the watermark. In asymmetric watermarking, different keys are used for embedding and detecting the watermark.
Robustness of Watermarking
Watermarking robustness is a measure of a watermarks ability to be virtually immune to a variety of processing operations or attacks. The watermark must remain through general signal processing operations (JPEG compression, cropping, etc.), geometric transformation and malicious attack.
Depending on its robustness, a watermark can be classified as fragile, semi-fragile or robust. A Fragile watermark cannot resist any attacks on the mark and may be manipulated before reaching the receiver. A semi-fragile watermark is able to endure certain types of attacking techniques and cannot resist some others. A Robust watermark is able to resist virtually all possible kinds of attack techniques.