VoIP communications can be captured by a lawful interception system at an ISP and distributed to authorized law enforcement destinations where the voice, video, fax and data network traffic can be decoded and interpreted. The architecture below illustrates the lawful interception apparatus and methods for a telecom traffic probe, analysis and capture of VoIP network traffic at an ISP.
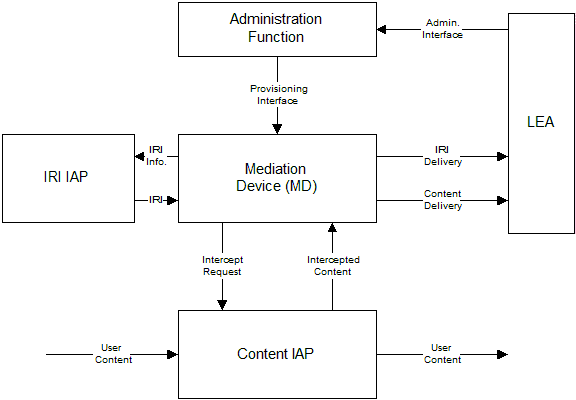
Lawful Interception Gateway delivers VoIP network traffic captured at an IAP to the LEA
The law enforcement agency (LEA) sends a request to the lawful intercept controller (system administrator). Based on the authorized level of access for the LEA and the request, either the lawful intercept related information (IRI), content or both is then collected by the respective intercept access point (IAP) and delivered by the lawful interception gateway to the LEA for processing.
Typically, automatic sniffer programs analyze telecommunications traffic and intercept data at access points on the digital segments of PSTN and on IP networks at routers and switches using port mirroring or network taps to capture the packet data at network speeds. Either method duplicates and diverts the packets without interfering with the original data stream. Traffic analysis ensures that either the entire data stream or only those packets that satisfy the frame capture filter criteria are acquired for further processing.
When the initial call information is placed, the system can detect the event and record this information as the IRI. If the LEA is only authorized to receive the IRI, this information is passed to the LEA along with any other lawful intercept related information. If the call information is to be collected, the IRI will contain information, such as the caller ID, IP address and encoding scheme, needed to find and track the call session.
Lawful Interception Requirements
Most nations have some requirement for lawful interception compliance and reporting standards that service providers must satisfy. In the United States, the Communications Assistance for Law Enforcement Act (CALEA) requires licensed telecommunications companies including common carriers, broadband Internet access and Voice over Internet Protocol (VoIP) service providers, to support lawful intercept efforts.
Requirements may vary across national and even state boundaries. Service providers must:
- Understand their obligations for each jurisdiction in which they operate.
- Coordinate intercepts with other providers and network operators.
- Handle targeted individuals that temporarily access their own network.
- Transfer, exchange or even suspend collection activities as the person of interest crosses jurisdictional boundaries.
Because of the sensitive nature, there are basic lawful intercept security, requirements, constraints and provisions which need to be met.
- Access Control: Only authorized entities should be allowed to access collected information. Also, there may be restrictions on WHAT information is to be passed to the LEA (for example, only the caller information). Finally, undelivered information must be kept in such a way that if power is lost, that information is destroyed.
- Accountability: All events and related information for authentication, access, transfer, exchange and destruction of lawful intercept information must be documented for compliance.
- Encryption Keys: Any encryption keys known by the service provider must also be passed to the LEA. In case of end-to-end encryption (i.e. using a key unknown to the service provider), the entire intercepted packet must be delivered.
- Secrecy: Intercepts must be done in such a way that the target or subject of interest is not aware that surveillance, monitoring and acquisition of communications is taking place.