There are two forms of SIP User Authentication – authentication of a user agent (UA) by a proxy, redirect, or registration server; and authentication of one UA by another. With Transport Layer Security (TLS), mutual authentication of proxies, or a proxy and UA, is accomplished using certificates. Authentication is used to allow only authorized access to a service or feature and prevent malicious or unauthorized use by other applications.
Digest Authentication
Digest authentication is a simple challenge/response method based on HTTP. For RFC 2069 “An Extension to HTTP : Digest Access Authentication”, it employs a MD5 hash algorithm to encode the username, realm, password, digest URI, and server generated nonce as follows:
- H1 = MD5(username : realm : password)
- H2 = MD5(method : digestURI)
- Response = MD5(H1 : nonce : H2
RFC 2617 “HTTP Authentication: Basic and Digest Access Authentication” added a client generated nonce and quality of protection (QoP) to improve security as follows:
- Response = MD5(H1 : nonce : nonceCount : nonceClient : QoP : H2)
RFC 7616 “HTTP Digest Access Authentication”, which replaces RFC 2617, added support for hashing with the SHA-256 and SHA-512-256 algorithms, allowing the inclusion of multiple headers per authentication challenge, improving security with stronger hashing while allowing backwards compatibility by allowing clients that lack support for the newer algorithms to choose the older ones.”
Authentication and Key Agreement (AKA)
RFC 3310 “Hypertext Transfer Protocol (HTTP) Digest Authentication Using Authentication and Key Agreement (AKA)”, created a framework for using digest authentication with an authentication and key agreement system (AKA), which adds additional security parameters RAND and AUTN. These form part of the nonce value, and allow mutual authentication of client and server. Voice over LTE (VOLTE) networks use this system to authenticate and register user equipment, such as mobile phones, when the equipment connects to the network.
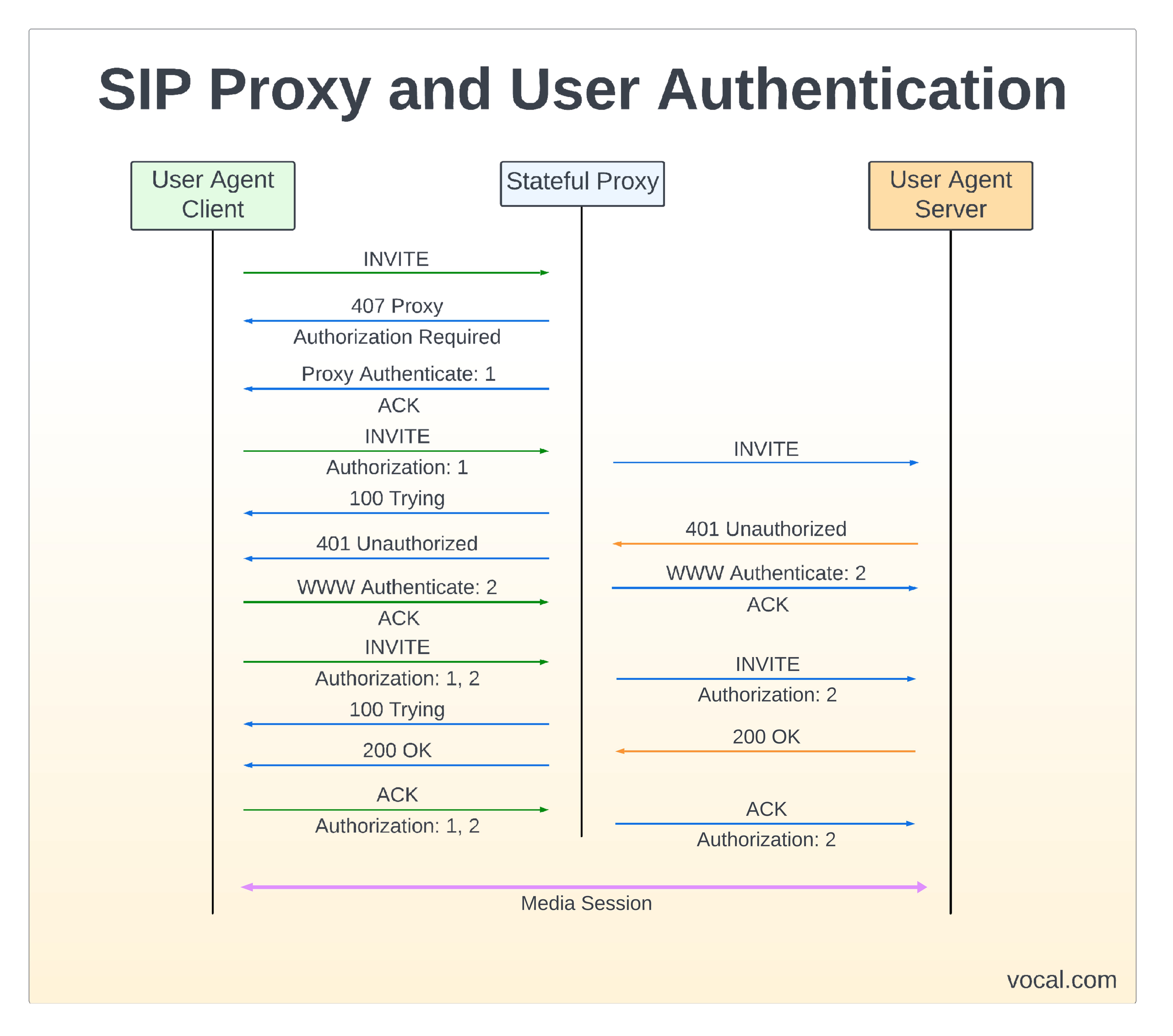
SIP Proxy and User Authentication
As depicted in the figure, the message flow for both proxy and user agent authentication is illustrated. The initial INVITE is challenged with a 407 Proxy authorization required. The UA responds with an ACK and then reissues the INVITE containing the authentication credentials. The next proxy server or end UA responds with a 401 Unauthorized message back to the source UA to again reissue the INVITE with the proper authentication credentials and complete the authentication process.
Authentication Features of VOCAL SIP Software Libraries
- RFC 3261 SIPv2 Compliant
- UE or Server implementations
- Full support for the latest authentication methods
- Supports end-to-end and hop-by-hop authentication
SIP Software
VOCAL’s SIP Software Libraries include a complete range of ETSI / ITU / IEEE compliant algorithms, in addition to many other standard and proprietary algorithms. Our SIP source code is optimized for execution on ANSI C and leading DSP architectures from Intel, ARM, TI, ADI, AMD, MIPS, and other vendors. The SIP software libraries are modular and can be executed as a single task under a variety of operating systems or standalone with its own microkernel.
More Information
- Session Initiation Protocol (SIP)
- SIP Analog Modem Server (SAMS)
- SIP Software Modules
- SIP Conferencing
- SIP Message Routing
- SIP Presence and Instant Messaging
- SIP Registration
- SIP User Authentication
- Secure SIP
- Session Initiation Protocol (SIP) and Deep Packet Inspection (DPI)
- SIP Trunking
- SIP Agents
- SIP Servers